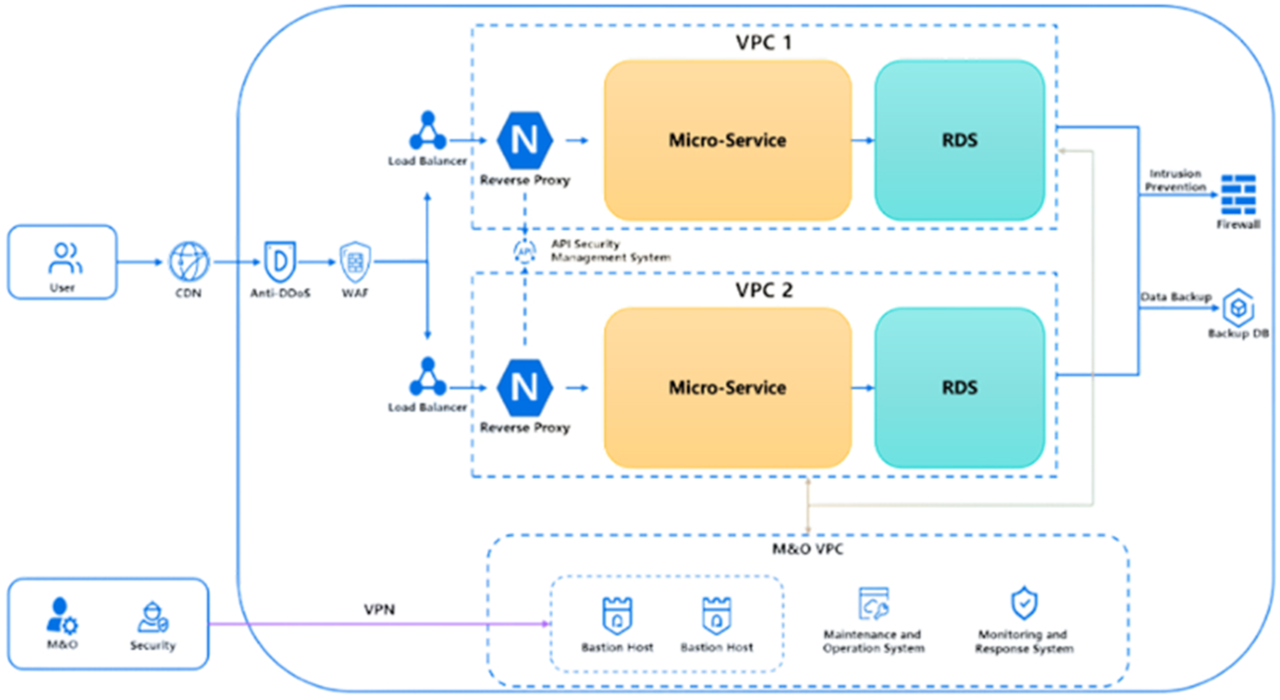
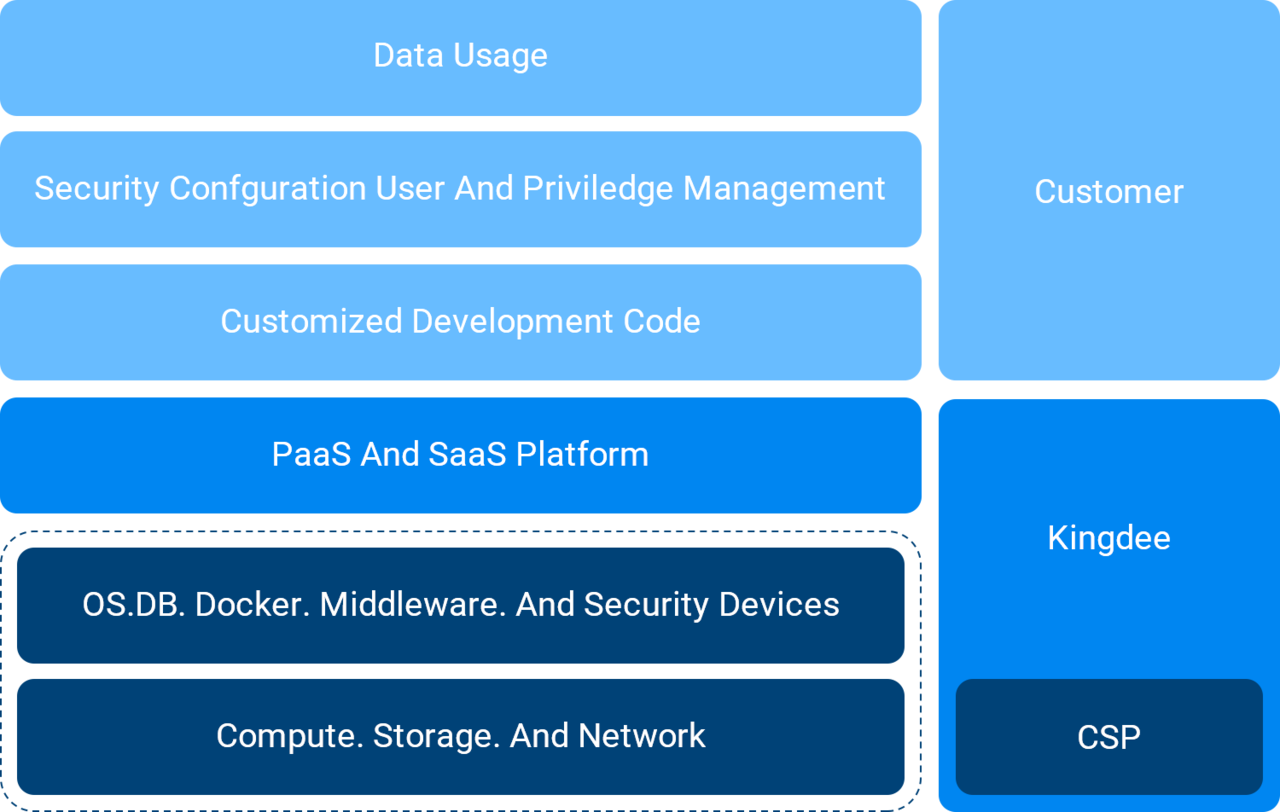
Information that could help us locate, identify or mitigate vulnerability such as requests with injection, screenshots of pop-out, prove-of-concept code, etc.
Your email will be confirmed as received within 24 hours and it may take a few days to verify the reported vulnerability. We will contact you through the sender’s email address if further communication or inform action is required.